Today’s article is all about Vishing attack and How to identify a Vishing Attack.
Additionally, we believed that it would be quite helpful for our users to have a comprehensive understanding of the Different types of common Vishing attacks.
Vishing is a sort of phishing scam in which online criminals call people on the phone without their consent to get personal information that they may use to perpetrate fraud, take over people’s identities, and steal money.
Alternatively, by inserting phone numbers in the phishing email, scammers may convince victims to follow up on the fake information in the message.
Vishing phone calls deceive victims by impersonating reputable businesses or individuals utilizing VoIP technologies, 800-numbers, and ID spoofing.
Once they get you on the phone, attackers frequently utilize social engineering strategies to persuade you to divulge private information like passwords and credit card data.
Vishing attacks can target anybody, although they frequently target the elderly and staff members who frequently interact with others outside of their business.
When I first learned about vishing, I wasn’t sure if it was distinct from phishing or if they were the same.
So, I did some research and found that these two terms are used to describe different types of cyberattacks.
However, the scammers target the victim for the same purpose in both phishing and vishing attacks.
Confusing? It isn’t… Hey don’t complain; as always, we have your back, readers.
Thus, while giving this a thought, we concluded that it was crucial to explain the distinctions between Phishing, Vishing, and Smishing so that it can save you from having to navigate across many sites to get their meanings.
What Is the Difference Between Phishing, Vishing, and Smishing?
In short, cybercriminals may utilize several channels for vishing, phishing, and smishing. Nevertheless, their objectives are the same: seizing control of accounts, committing fraud, or looting trusting people and organizations.
The three methods differ as follows:
-
Vishing

Scam phone calls that force victims to verbally divulge private information. Vishing is also known as “Voice Phishing.” Therefore, keep hold not to muddle the two terms. Vishing is occasionally considered to be a kind of phishing as well.
-
Phishing
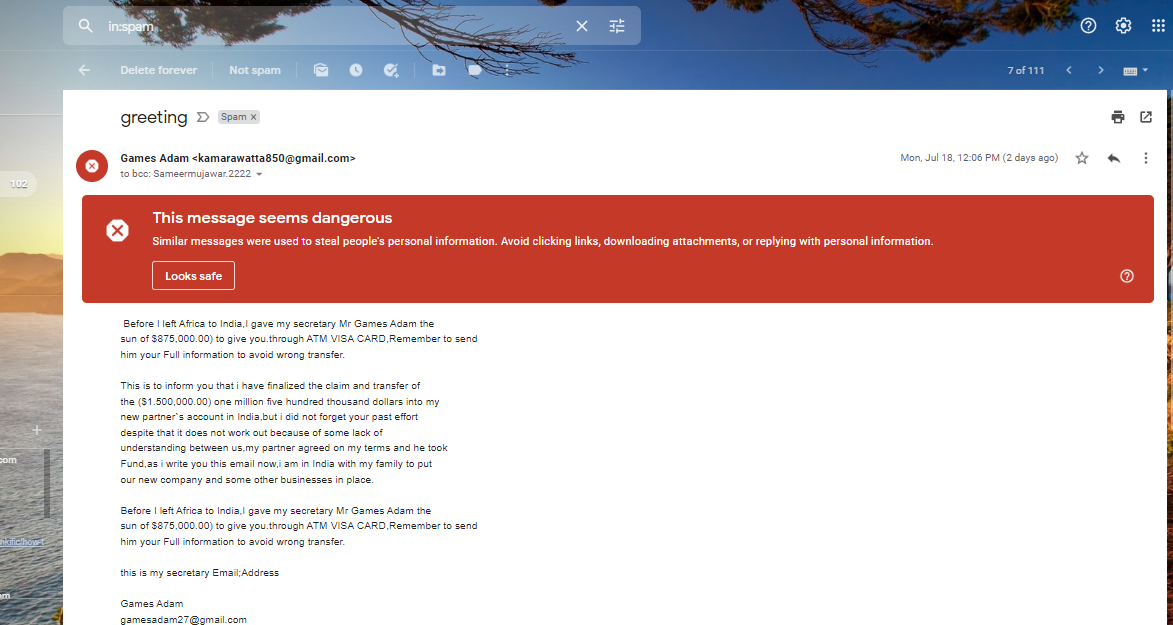
Email scams that persuade victims to click on malicious links or go to bogus websites (pharming). If you learn the common indicators of phishing attempts, you can certainly protect yourself from being a trapped by the actors a.k.a hackers.
-
Smishing
Scams using text messages to lure victims into visiting phony websites or clicking on harmful links.
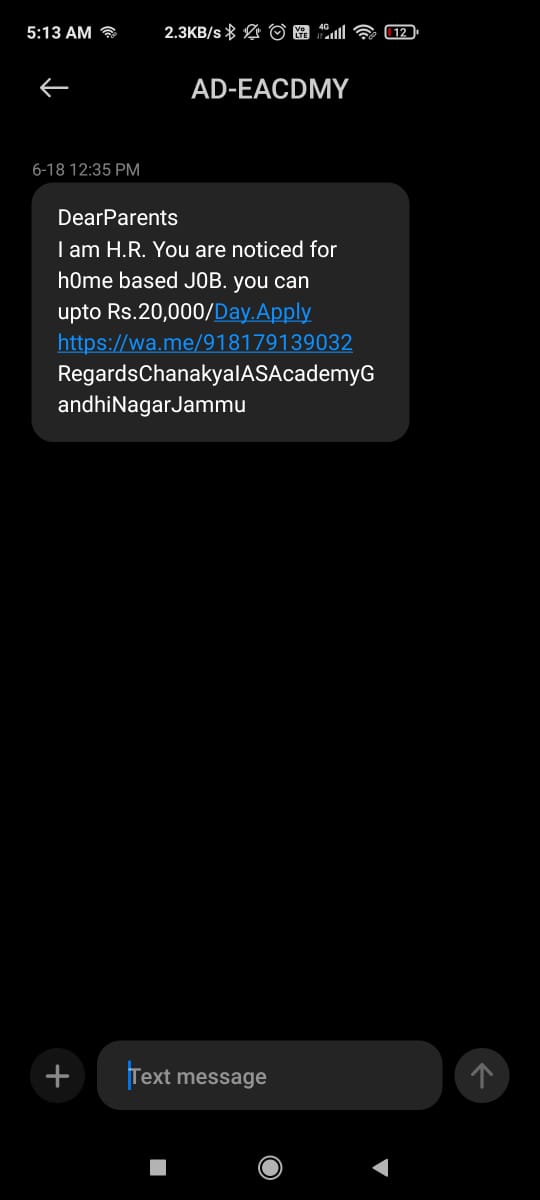
Common Vishing Scams
-
Bank Account Theft

The scam artist poses as a representative of your bank and claims that there is a problem with your account or that it has been compromised.
-
Posing a threat to law enforcement
A scammer can pose as a law enforcement official and suggest that they are working to help the person avoid facing criminal charges, but they need some private information to get started.
-
Taking the Place of Government Officials
Pretending to be from the Internal Revenue Service (IRS) and telling a victim that there is a problem with their taxes that can be resolved by giving the con artist private information is a typical approach.
-
Technology Support Attacks
Scammers pretend to be employees of firms like Apple, Microsoft, and Google in tech support vishing attempts to alert you to unusual activities on your online account.
Additionally, they frequently request an email address in order to deliver software updates that end up being malware downloads.
Bank Impersonation Scam
Scammers pretend to be banks, credit card companies, and other financial organizations in order to get access to your accounts.
The scammers alert you that there has been suspicious activity and request that you validate your account details and login credentials in order to “correct” the issue.
Common Vishing Techniques
-
Wardialing
A message involving a nearby bank, company, police station, or other local institution is used by the attacker to dial certain area codes using software.
-
Caller ID forgery
The attacker uses caller ID counterfeiting to conceal himself behind a false phone number, similar to VoIP vishing. They could put their name down as Unknown or use an ID that says “Government, Tax Department, Police, etc.” to seem to be a real caller.
-
VoIP

Scammer may easily generate fictitious numbers and hide behind them thanks to VoIP. These numbers are difficult to trace and can be used to generate phone numbers with a 1-800 prefix or that seem local.
-
Diving into trash
Digging through trash behind banks, offices, and other odd institutions is a straightforward and well-liked technique for gathering legitimate phone numbers. Criminals frequently gather enough information to launch a focused spear phishing assault on the victim.
How to identify a Vishing Attack

A vishing attack is difficult to recognize. We frequently fall victim to these hackers’ traps.
They have trained voices and excellent techniques to make you think they are from reliable sources rather than some random fraudsters, so believe me on this.
-
Demanding Voice and Sense of urgency
Analyse whether the caller’s tone exudes a feeling of desperate urgency. Scammers attempt to use fear and panic to get victims to cooperate by creating situations where there may be legal trouble or bank account troubles.
The success of a vishing assault frequently depends on inducing fear in the target or exerting other forms of pressure.
Offers that are time-sensitive or provide a solution to a pressing issue may fall under this category.
Proceed cautiously and with caution if you are being threatened with account suspension, arrest, or demands for urgent payment.
On the other side, scammers who prey on your kindness and good will over the phone might fool you into giving them access to your personal information and financial accounts.
No matter how nice you believe they are being, if you feel you are disclosing too much information to an unidentified or suspicious individual over the phone, be wary and hang up.
-
Information Request for Confidential Use
It might seem apparent, but if the caller requests information from you such as your name, date of birth, address, credit card information, or social security number, it is a tell-tale indicator of a vishing attack.
You should always be sceptical if a caller requests personal information. It’s sometimes impossible to tell for certain if a request is genuine or a victim of a vishing scam. To decline is better.
The Caller Claims to Be from Medicare, the Social Security Administration, or the IRS.
People frequently trust each of these groups and feel at ease disclosing personal information to them.
Real IRS, Medicare, or Social Security representatives will already be equipped with sufficient personal data to conduct business with you.
-
Unknown government agency
If a caller claims to be from the IRS, Medicare, or Social Security Administration but you haven’t given those organizations permission to contact you, it’s probably a fraud.
-
Nobody offers you anything for nothing
Pose inquiries. Ask the caller for identification that you can use to confirm who they are and where they work if they are attempting to sell you anything or give you something for free. Hang up if the caller declines to disclose this information.
Before giving the caller your information, make cautious to double-check any information they may have given you.
Safeguarding against Vishing Attacks
User knowledge is crucial for prevention and security against this social engineering assault as well as other types.
A well-known proverb states that “prevention is better than treatment.” It is something we should learn to do in our daily lives, especially when it comes to our bank accounts and other private information. As a result, we urge you to take the following actions to protect yourself.
- Never divulge personal information
- Constantly confirm phone numbers
- Never grant remote access to computers
- File Suspected Incident Reports
- Don’t Panic in such situations
- As many questions as you can
- Ask for assistance from others around you.
- Never reply to emails or messages on social media that request your phone number.
Conclusion
In our article we have explained everything related to vishing attacks and How to identify a vishing attack.
Vishing, sometimes known as “voice phishing,” is the practice of scamming others over the phone in order to get sensitive information.
Vishing, according to this definition, refers to a type of attack where the attacker tries to obtain the victim’s data and utilize it for personal gain, usually financial gain.
Human awareness is one of the primary lines of defence against phishing assaults.
Vishing and social engineering assaults may be very predictable, therefore knowing the tell-tale indications of these attacks can help you safeguard your privacy and the reputation of your business.
A legitimate business or its representative will never use phrases like “you will be sued” or “your account will be temporarily suspended”.
Therefore, be careful not to fall victim to these attackers’ traps. We must actually handle these circumstances calmly and seek guidance from closed ones. Try to avoid calls from spammer lists of numbers, and if you can’t, don’t answer them for extended period of time.
We sincerely hope you liked our article and would appreciate it if you would recommend to some personal friends and family members.







