What is a Common Indicator of a Phishing Attempt? (Podcast)
Knowing what is a common indicator of a phishing attempt is the most important when you have to depend on the internet.
There has been a spike in the number of cybercrime cases worldwide after the pandemic crippled the global economy.
Phishing Attacks are the most common ones you might have encountered. If not, check your mailbox again and keep counting how many strangers asked you to either invest in a scheme or purchase their service.
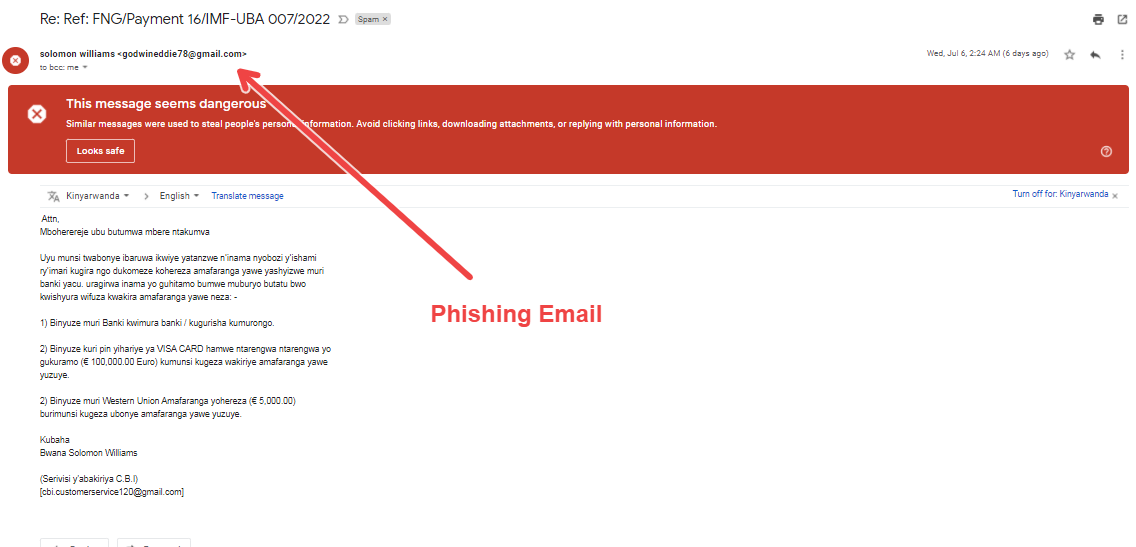
Ever wonder where they collect your details and send an email? Well, that’s what a common indicator of phishing attempt is.
Let’ Talk About What is Phishing Attack
Before finding an answer to your query, it’s more important for you to get to know the term. Because just like fishing, cybercriminals use bait to get your financial details.
Generally, a phishing scam is used to get your details by triggering you to perform an action.
Once you do it, you are caught off-guard. Voila, the scammers have their smoked salmon or tuna salad ready for dinner.
Although phishing scams are not new, the number of phishing attacks has risen by 59% globally during the pandemic alone, reports Interpol.
Threat actors behind have taken a new approach into account by generating COVID-19 themed phishing emails, often impersonating government and health authorities.
You can get the rest of the idea by checking into your mailbox. The usual messages can be as pleasing as, “Congratulations, you have won $10000, click here to claim your prize,” or “Congratulations, your loan is approved.”
Different indicators of Phishing Scams
If you have been working from home due to lockdown restrictions, you must have received some emails.
If you are one of the concerned ones willing to know common indicator of a phishing attempt, here are some answers to suffice.
Following are some Phishing attack examples you can identify in your received emails.
- A modified brand logo
- A shortened link
- A document in attachment
- Minimal content in the message body
- Attractive catchphrase
- Unknown charity organization
- Use of jargon language
Different Types of Phishing
The top-most common indicators of phishing attempt is tone of text, poor grammar and sense of urgency in email body and subject line. Major warning signs are : Mispelled words, jargon language and common greetings like Hi sir/madam, hi buddy etc..
Now lets learn about the phishing then we will learn best ways to protect ourselves from phishing attack.
1. Email phishing (Targeting organizations/Individuals)
Most phishing attacks are sent via email. The actor registers a fake domain that copies a genuine organization and spams thousands of generic requests.
They can’t use the exact domain name but identical ones. For example, they might use the organization’s name in the local part of the email address (such as paypal@domainregistrar.com). This means when you receive their mail, the username will show up as PayPal.
One of the common indicators of phishing attempt is greetings, and the signature in the email sounds more “generic,” Like dear sir/madam, dear customer, dear client, etc.
Usually, no any organization sends their customer/client this kind of generic greetings; they typically call their customer/client by their names.
Any genuine organization if send any mail, then there will be a contact number at the signature block.
If you see the mail and missing contact information at the signature block, then it might be a “Phishing Attempt.”
If you see any anonymous email with unsolicited/unnecessary an attachment, then that email might be the “phishing attempt.”
Because cybercriminals do this, and if you click on the attachment, then it will get downloaded to your personal/professional computer, and your information will get compromised.
Some tricky hyperlinks/websites have been used in the body of the email. Like if you take the cursor over the link, then it may show a different web address.
The websites containing malware that uses similar domain names with different variations such as, instead of “.com,” may use “.net.” Hackers use “URL shortening services” to conceal their true link’s destination.
If you closely look at the “phishing email,” then you will encounter poor grammar and many spelling mistakes.
The genuine organization uses any grammar tool or makes proofreading before sending any professional email. So this is also one of the common signals of phishing attempts.
2. Spear Phishing (Targeting Important Persons)
This is one of the types of phishing attacks in which the actor has some information of the target users, such as their names, Place, Job Details, or email address.
And the actor uses that specific information to make a phishing attack. In this type of phishing, a cybercriminal sends an email that appears from a trusted source and leads to malicious websites.
For example, you may get an email from a bank telling you that “your account has been compromised” re-enter your username and password to protect your bank account.
It seems that this is a genuine email but remember, no any bank asks their customers to enter their personal information over an email, so it is a phishing email.
If you give your information, the actor may steal your money and even your identity to perform other illegal activities.
If you receive these kinds of emails, just ignore them and mark them as spam. The hacking incident of the Democratic National Committee in 2016.
What appeared as simple updates from Google turned out as emails sent by the Russian hackers to the committee members.
Read Related: What Helps Protect From Spear Phishing?
3. Whaling
This phishing attempt is similar to the previous ones; however, the only difference is that it’s more targeted to a highly influential person in an organization such as CEOs, Directors, or heads of the organizations.
The actor pretends to be a senior-level staff to leave a big impact on the recipient. Tax return scams most commonly fall under this category.
In this case, you may receive an email telling you need to file you tax return before the deadline and click here to make your tax return now.
There are kinds of sense of urgency they will create in the email so that victims may think less, take action, and fall into their trap. And one more example of “Whaling,” you may get an email from a trusted source.
For example, an employee may get an email from the company’s CEO asking for payroll information.
And if top-level authority is asking and everything seems very much genuine, then you may fall into the trap of “Whaling” type of phishing. These are some examples of common indicators of a phishing attempt.
4. Smishing and Vishing
Smishing and vishing refer to when the method of scamming changes to text and telephonic conversations.
However, the content and intent of the message are the same. Smishing involves the text message, while vishing involves a telephonic conversation.
In a vishing scam, an actor pretends to be from a reputed agency, convincing the victim that their account has been compromised.
The Microsoft tech support scams are the most common Phishing Attacks examples. Check Jim Browning’s YouTube channel for more awareness.
-
Angler Phishing
This attack uses social media platforms to trick victims. This attack can be carried out in multiple ways through fake URLs, cloned websites, social media posts, or tweets.
All these platforms can convince victims to divulge sensitive information or download malware onto their systems.
Angler Phishing is easiest for cybercriminals as they mine user’s information through the information shared on social networking sites.
Protecting your organization has become extremely important in order to avoid these kinds of phishing scams.
We recommend using the best possible protection to combat phishing and ransomware. So that your shield will be in place in order to defend against these phishing and ransomware attacks.
How can businesses improve their Phishing Security?
If you wish to stop further phishing emails and malware you’ll need a sophisticated email security system.
The security gateway for email is the initial option to protect yourself from malicious email, but it’s not required to invest a lot to secure your email.
If you’re on a budget or need to cut costs on security for your email, TitanHQ is here to assist.
SpamTitan has been awarded as an advanced email security system that blocks more than 99.97 percent of spam emails and also spam.
The software is simple to install set up, manage, and use. The pricing policy is straightforward and very competitive and with TitanHQ you’ll receive world-class customer support. You can also try SpamTitan for free to test its effectiveness for yourself.
Have You Ever Thought About Your Smartphone Security?
On a smartphone, you may be less cautious compare to computers. But phishing threats are similar to your smartphone also.
You may get an email if imitating the same characteristics mentioned above at “Email Phishing,” and you entertain that email by clicking and downloading an attachment, then your information will get compromised.
We are not that aware while checking emails over a smartphone, and you may pay less attention to your smartphone because of a small screen.
But by making one phone call/ opening a malicious email attachment,/ opening a malicious website will cause harm to your privacy.
So make sure you are paying extra attention while doing any online activities that may cause compromise your personal information.
What Do Hackers Want?
With the help of phishing, hackers do collect user’s information such as usernames, passwords, etc. And this information usually sells over the dark web.
The dark web is nothing but a deep internet network where information can be reciprocated/ data processed anonymously.
Collecting information individually becomes difficult thereby, hackers use social media. They create one downloadable file/link and give some fascinating offers along with it.
So that users get attracted towards it and download that executable file or click on the link and redirected towards the website where malware gets downloaded in his system automatically and his all information get compromised.
By understanding what is a common indicator of a phishing attempt, you will be well aware with the hackers’ different methods of stealing personal information.
One of the most common intents of hackers to do phishing attempt on the users is to make a ransomware attack on the system.
Now you need to understand what ransomware is? Ransomware is the kind of malware that encrypts the user’s system and demands a “Ransom,” which is often paid in bitcoins.
A fair warning by Interpol
- The story just doesn’t end here; the report issued by Interpol warns about more phishing attempts in the near future.
- Cybercriminals are likely to continue to run coronavirus-themed online scams and phishing campaigns to misuse people’s fear amid the growing pandemic crisis.
- There will be another spike in phishing related to medical products related to the COVID-19 vaccine, as well as network intrusion and cyberattacks to steal data.
Have You Found What is a Common Indicator of a Phishing Attempt?
The information pretty much answers the commonest ways to spot a phishing attempt, whether you’re working from home or studying for your college. All the phishing attempts aim at one ultimate target, and that’s your personal information or card details.
Otherwise, phishing attempts are targeted to obtain employee login information or other details to damage an organization’s goodwill or carry out an attack against a specific company. Advanced Persistent Threats (APTs) and Ransomware are common starts with phishing attempts.
How to Prevent Phishing Attacks?
It Seems Merely Knowing Iot And Internet Terminology Is Not Enough To Protect Yourself From Looming Online Threats. As An Employee, You Should Educate Yourself About The Potential Risks Involved In Phishing Scams. Identifying Phishing Emails And How Not To Falling Victim To Scammers Are The Most Important Things. Real-Case Scenarios And Simulations In A Working Environment Must Be Exercised To Avoid Future Mishaps.
No Single Cybersecurity Technology Can Work Single-Handedly To Prevent Phishing Attempts. Organizations Need To Have A Multi-Layered & Multi-Dimensional Approach To Circumcise The Number Of Attacks And Limit Their Impact.
Besides Implementing Network Security Methods Such As Email & Web Security, Malware Protection, User Behavior Monitoring, Or Access Control, Professionals Should Also Use Their Intelligence To Play Their Part In A Secured Environment. Identifying a common indicator of a phishing attempt is a good start to stay. I hope now you got the answer to, “What is a Common Indicator of a Phishing Attempt?”.
Bonus Tips To Avoid Phishing Attempts
- One of the most common signals of phishing attempts was “suspicious email attachments” that may be images/zip files etc. Make sure you have disabled your MS Outlook/ Gmail automatic downloading of images.
- No matter if your organization is small in size or mid-sized, cybercriminals target everyone. Make sure that you have spam and malware filters.
- Suppose you have only a single way of authentication. In that case, it may create trouble if your personal information gets compromised because actor can easily enter at your system—one of the best way to ON multi-factor authentication. If anyone anonymously tries to log in to the system, you will get asked for final confirmation. That’s how you will get saved from the system’s security breach. Make sure you are making multi-factor authentication enabled everywhere you can.
- Sometimes you may face a condition where changing password immediately is important. At that time, corporate password manager helps to change passwords quickly and avoid further data breaching by cybercriminals.
- You need to train your team to make them aware of what is common indicator of a phishing attempt. Awareness may reduce phishing attacks by cybercriminals. Ensure you are arranging seminars by cyber experts for your team to understand “Common Indicators of Phishing Attempts.”
Why Is It Important to Be Aware of Phishing?
Phishing is the kind of cyberattack workers see the most. Cybercriminals favor phishing because it has a low limit to segment, it’s unobtrusive and it’s compelling. Phishing is a simple way for troublemakers to get passwords, client information, and different accreditations, empowering them to embrace other cybercrime activities like business email splitting the difference, or sending ransomware. An expected 75% of associations in the United States were hit by a phishing assault that brought about an information break in 2020.
How Can I Safeguard My Company from Phishing Attacks at a low cost?
Safeguarding your business, and is a snap when you pick computerized, AI-controlled email security with Graphus.
Automatic Phishing Security with Graphus
Graphus has a range of advantages for companies of any size. It keeps any phishing attempts out of your company and out of your employees. It also allows your employees to stop a phishing attack if they discover the signs. Graphus comes with three layers of protection that protect an email that is phishing and your company.
TrustGraph employs more than 50 different points of comparison to identify malicious messages before they get to the inboxes of employees.
EmployeeShield includes a bright and noticeable box that reminds employees to exercise caution when handling messages that come in.
Phish911 makes it simple for workers to notify any suspect messages they receive and email to an administrator who can assist them.
Read Related: What to Do if You Click on a Phishing Link? [Learn Quickly]
Conclusion
I hope you got the clear answer for, “what is a common indicator of a phishing attempt ? “.
Make sure you are giving high priority to your private/firm’s security. Because if any cybercriminal became successful in making a phishing attempt, then you/your firm would suffer from a data breach, financial loss, reputation damage, etc. To avoid these all bad things, make sure you have powerful security.








