In the digital age, the secure transfer of files is paramount. Whether you’re a corporation guarding trade secrets, a small business sharing financial data, or an individual sending personal information, security cannot be compromised. Enter Secure File Transfer Protocol (SFTP), a robust solution ensuring the integrity and confidentiality of your data in transit. This comprehensive guide serves as a beacon through the technical fog, transforming the esoteric into the accessible. Journey with us as we unravel SFTP, presenting a must-have knowledge toolkit for anyone looking to safeguard their digital exchanges.
What is SFTP?
SFTP stands for Secure File Transfer Protocol, an advanced protocol that operates as an armored courier for your data. Think of Secure File Transfer Protocol as a fortified van for online information, where data is not just locked inside but also encrypted, so it’s unreadable if intercepted. The essence of SFTP lies in its ability to shield data from prying eyes during the perilous journey across the internet. It’s the digital equivalent of sending a letter in a tamper-proof envelope, providing peace of mind that private information remains confidential.
How Does SFTP Work?
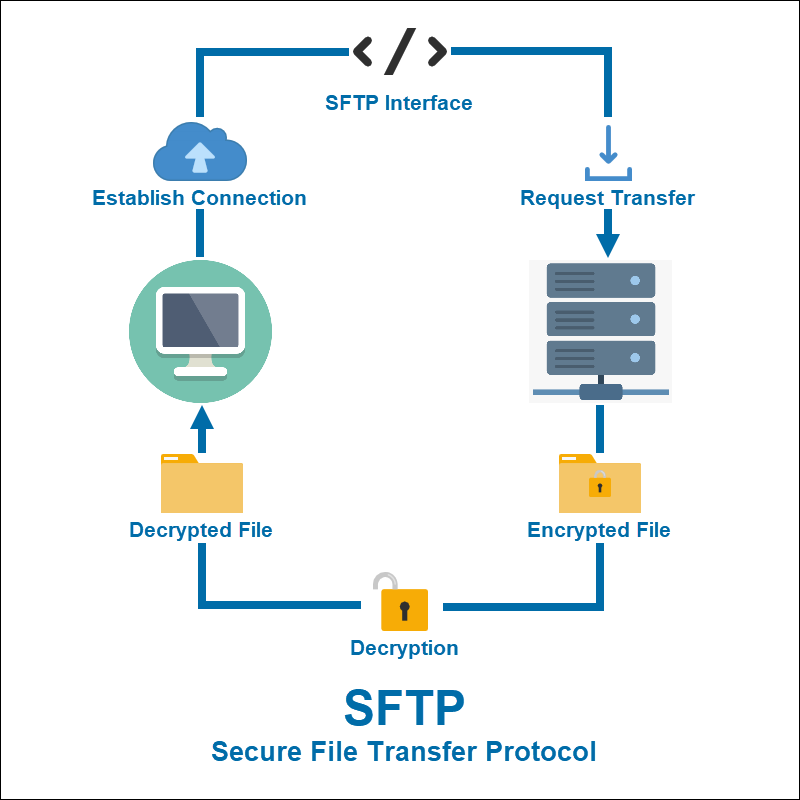
SFTP is not your ordinary file transfer butler; it’s a digital bodyguard that ensures your files arrive untampered and secure. Imagine your data wrapped in a cryptographic envelope as it traverses the network. Secure File Transfer Protocol leverages powerful encryption, making your files unreadable to unauthorized eyes. Authentication is like a secret handshake between the server and client, confirming identities before any data is exchanged. This duo of encryption and authentication fortifies file transfers against eavesdropping and unauthorized access, making SFTP a bulwark of data security.
Key Advantages of SFTP
SFTP is not just a protocol; it’s a fortress for file transfer. It brings a slew of benefits to the table, not the least of which is ironclad security. With SFTP, data is encrypted before it leaves your outpost, ensuring it’s impervious to interception. But the merits don’t end there. SFTP boasts exceptional reliability, resuming transfers even after interruptions. Its platform independence makes it a versatile tool for various systems, unshackling users from the confines of any single operating environment. This trio of advantages makes SFTP an unparalleled choice for secure file transfer.
Setting Up an SFTP Server
Establishing a Secure File Transfer Protocol server is akin to constructing a digital fortress. First, select your bastion—popular server software such as OpenSSH or Bitvise. Install the chosen software on the host machine, typically a server with robust security features. Configure the server settings, paying meticulous attention to the encryption algorithms and authentication options to strengthen the fortifications. Assign user access permissions, crafting a landscape of drawbridges and moats that dictate who can enter your digital keep. With these steps, your Secure File Transfer Protocol server stands ready, a sentry for secure file transfers.
SFTP Clients: How to Connect
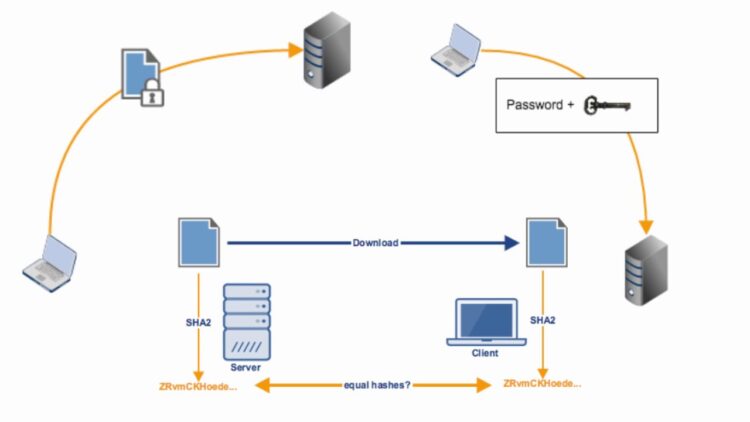
To connect to the SFTP server, you need a Secure File Transfer Protocol client—your key to the digital stronghold. First, choose a reputable client tool, such as FileZilla or WinSCP, and install it on your computer. Open the client and input the server’s address, port number, and your credentials—username and password or a private key if key-based authentication is in play. Upon connecting, a secure tunnel is established, through which your files can traverse safely. Your SFTP client is now a loyal envoy, adeptly handling your files within the secure confines of the server.
Authentication Methods
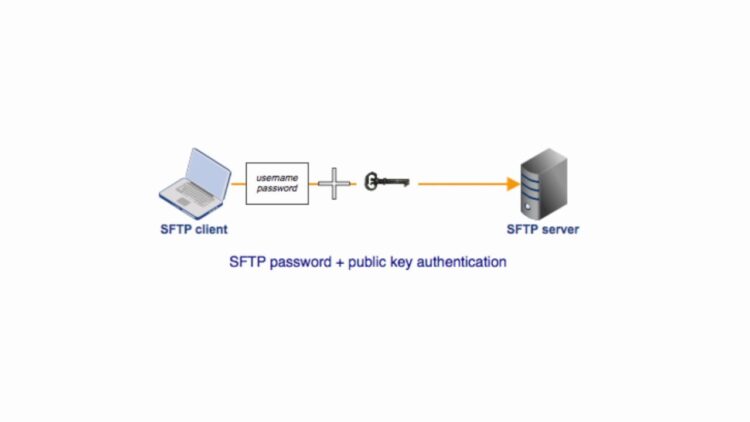
Authentication in SFTP is the checkpoint ensuring that only authorized personnel handle your digital assets. The traditional method is password-based, where a correct username-password combination grants access. However, key-based authentication offers a more robust alternative. Here, a pair of digital keys—a private one you guard closely and a public one you distribute—works in concert to authenticate access. This method is akin to a two-tier security system where what you know (password) can be complemented by what you have (keys), thus fortifying your defense against unauthorized access.
File Transfer Commands
Within the realm of SFTP, commands act as the trusted couriers managing your files. Essential commands include put for uploading files to the server, get for downloading, and ls or dir for listing directory contents. Each command is a directive, telling your SFTP client how to handle your precious data. For instance, rename changes file names, mkdir creates new directories, and rm deletes files. Mastery of these commands empowers users to navigate the Secure File Transfer Protocol landscape, orchestrating file transfers with precision and control.
Common SFTP Use Cases

SFTP serves a multitude of scenarios. Businesses employ it for secure backups, ensuring their operational continuities. It’s a vessel for data sharing among trusted parties, maintaining confidentiality. For the tech-savvy, automated transfers via scripts or batch jobs keep the digital workflow seamless. Consider healthcare providers who rely on Secure File Transfer Protocol to transmit sensitive patient records—compliance and privacy are not just a priority but a mandate. In each use case, SFTP proves to be not just useful, but critical for secure, reliable data handling.
Troubleshooting SFTP Issues
Even the most fortified castles have their weak points, and SFTP is no exception. Common issues include connection problems, often remedied by verifying network settings and authentication credentials. Permission errors may arise, necessitating a review of user rights and file ownership. Transfer interruptions can occur, typically addressed by configuring timeout settings and ensuring stable connectivity. When faced with these challenges, a systematic approach to troubleshooting—assessing logs, checking configurations, and updating software—can restore the fortress to its full function.
Best Practices for SFTP Security

In fortifying your Secure File Transfer Protocol setup, vigilance is key. Regular updates to the server and client software patch vulnerabilities, reinforce your ramparts. Employ robust authentication methods and strong, complex passwords to ensure only the right knights gain entry to the keep. Manage user permissions with precision, granting the least privilege necessary to perform tasks. Regularly audit logs for suspicious activity, staying alert to potential breaches. These best practices form the bedrock of your SFTP security strategy, ensuring your digital fortress remains impervious to threats.
Conclusion
Secure File Transfer Protocol (SFTP) stands as a sentinel in the digital landscape, guarding against the threats that imperil our data. Through this guide, we’ve illuminated its workings, from the intricacies of setting up a server to the nuances of client connections, authentication, and beyond. Armed with this knowledge, you’re now equipped to deploy SFTP in your digital arsenal, ensuring that your file transfers are not just successful but secured. Embrace this protocol, and let the shield of Secure File Transfer Protocol safeguard your digital exchanges in this ever-connected world.