The increasing use of remote work following the pandemic has created secure remote access solutions essential for many companies.
While many organizations have employed virtual private networks (VPNs) for remote accessibility, zero-trust network access (Zero Trust Network) is an option that is more suitable to the requirements of many companies.
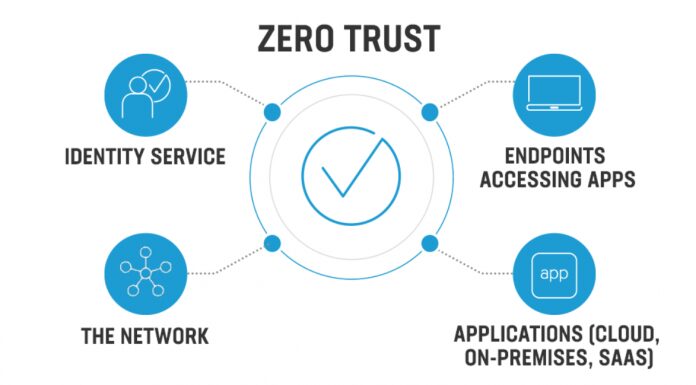
What exactly is Zero trust Network?
Zero Trust Network is an encrypted remote access solution that utilizes zero-trust security principles, with specific permissions for applications. Remote workers. Who must access to assets of the company will be granted access to specific resources on a case-by-case basis? Taking into account roles-based access controls as well as contextual authentication data such as IP address location, user group, or role, as well as time limits.
What is a VPN?
VPNs offer remote users an experience that is like a connected company network. VPNs, the VPN software client, and VPN endpoints that are connected to the corporate network. Create an encrypted channel through which every data transmission is encrypted before it is routed to the destination. This prevents eavesdropping and allows all business data to be scrutinized by perimeter-based security software regardless of the source.
Is the VPN In the End? VPN Vs Zero Trust
The primary difference between VPN options and zero Trust is that Zero Trust provides security and agility for businesses but VPNs are susceptible to data breaches and make users slow. VPNs are virtual private networks utilized by companies to connect remote employees.
But, VPNs aren’t able to address all the complicated and dynamic needs of modern companies. Solutions that are based around Zero Trust access can complement or completely replace VPNs to provide secure access to data and better business flexibility. This blog will provide the reasons. why it’s important to choose the right connectivity solution that’s more secure and efficient than VPN.
First, let’s look at what VPNs are and what they’re not.
VPN Vs Zero Trust network
VPNs offer every user an authentic login password for full network access. In the case of cyberattacks, Zero trust Network restricts access to specific apps. which reduces the exposure of personal data and threats to lateral movement?
VPNs are not restricted at the app level and provide no insight into user behavior once they are within their private networks. Zero Trust vs VPN Networks watch every action of users and offer greater transparency and surveillance of user behavior and threats, allowing more informed, data-driven control to protect sensitive information within applications. Logs can be integrated into we will give a complete analysis of the user’s activities and threats in real-time.
Zero Trust Networks are also able to be linked with an endpoint security system to allow for an adaptive access system based on the regular assessments of the security posture of devices.
VPN connections don’t take into account the risk posed by devices used by the end-user when assessing the endpoint’s security. Devices that have been compromised or infected by malware could connect to the server and gain the access it needs to its internal resources.
ZTNAs check the devices they connect to regularly, verifying their security status and allowing flexible access to resources according to the trust of the device at the time. If there is a risk and the device is connected, it’s immediately terminated.
VPNs aren’t designed to support today’s dispersed workforce. Each user’s connection that is routed through central VPN hubs can cause issues with performance and bandwidth and an unsatisfactory user experience.
Users can establish direct-to-app connections through ZTNA that allows quick and secure access to corporate data stored inside IaaS setting or in private data centers and also flexible and flexible cloud deployments.
Read More: How to implement a zero trust network.
Zero Trust Network reduces costs by eliminating the necessity to buy costly VPN equipment and management. the complex infrastructure configuration in every data center. Besides, remote users must not separate intensive VPN software to establish secure connections.