In today’s article, we’ll go into extensive detail concerning the Social Engineering and what can be possible Best ways to protect yourself from Social Engineering.
Cybercriminals utilize social engineering, a type of psychological manipulation, to trick unwary users into breaching security and handing over their private information.
Using human emotions like fear, curiosity, greed, rage, etc., a criminal might lure people into clicking harmful links or falling prey to physical tailgating attacks.
Over the years, these attacks on businesses have increased in frequency. In actuality, it has become more complex than it seems to be.
Security personnel should be aware of each user’s activities to intervene, if necessary, as social engineering is a burgeoning area and your users are your final line of defence.
However, it is your duty as the end user to keep an eye on your own behaviour.
It goes without saying that there won’t be a “stop sign” for cybercrimes any time soon.
Instead, hackers are coming up with increasingly inventive ways to trick users into giving private information.
Thus it has become imperative that businesses also carry out thorough research and use the appropriate equipment to stay one step ahead of criminals.
Most of us consider our defence against hackers that target data networks through technological flaws when we think about cyber-security.
However, there is another approach of entering networks and organizations: preying on people’s vulnerabilities.
The practice of persuading someone into disclosing information or granting access to data networks is referred to as Social Engineering.
For instance, a thief may request consumers for information like their usernames and passwords while posing as IT support workers.
And it’s really surprising how many individuals aren’t hesitant to offer such information, especially if it appears that a respectable person is asking for it.
Simply put, Social Engineering is the use of deceit to trick someone into giving over information or data or granting access.
The majority of organizations are aware of cyberattacks and have made many significant investments in security measures to lessen security threats.
Despite this, there is still an integral part known as the human in the digital world.
Attackers are circumventing the security layer by taking advantage of human weaknesses in the enterprises.
A social engineering attack is one that involves hacking a person

The two main objectives of social engineering attackers are:
1. They seek to steal information and money.
2. They want to manipulate data to inconvenience an organization. or get access without being asked.
Typical Social Engineering Attack Methods
-
Phishing
The most prevalent and effective social engineering assault is phishing. The fraudster utilizes cunning and deceit to induce a person or organization to reveal their PII and other assets via email, chat, online ads, or websites.
-
Spear Phishing
Another social engineering technique, spear phishing involves the fraudster doing some background research on the victim’s personal and professional life in order to create the most plausible pretext.
“Spear phishing” asks for private information from a single individual within a corporation by sending an email that appears to be from a higher-level boss.
For instance, the con artist can admit to the victim that they are organizing a surprise Anniversary party for a common friend and need assistance to make it happen.
-
Vishing and Smishing
These social engineering attacks are variations on phishing, or “voice fishing,” which involves merely calling a number and requesting information.
The offender could pretend to be a co-worker, such claiming to be with the IT helpdesk and requesting login details.
Instead of using emails to try to collect this information, Smishing employs SMS texts.
Read More: How To Identify a Vishing Attack & Safeguard Against it? (2024)
-
Contact spamming and email hacking
In this kind of attack, contacts are accessed through breaking into a person’s email or social media accounts.
It’s possible for contacts to be informed that a person has been robbed and has lost all of their credit cards before asking them to wire money to a money transfer account. Or the “friend” can send a link to a “must-watch video” that really leads to spyware or a keylogging Trojan.
Read Related : What To Do if A Scammer Has Your Email Address? [2023]
-
Hunting vs. farming
Always be aware that certain social engineering assaults are far more sophisticated. The majority of the easy methods we’ve discussed are a type of “hunting.” In other words, enter, take what you need, and leave.
To obtain more information over a longer period of time, some social engineering tactics, however, entail building a rapport with the victim.
Farming is what it is called, and it is riskier for the attacker since there is a greater likelihood that they will be discovered. However, if their intrusion is successful, it may yield far more information.
-
Baiting
When a fraudster utilizes false promises to entice a victim into giving up their login information, they are said to be using baiting.
For instance, the fraudster may place a flash drive (or bait) that has been infected with malware but seems real in the least suspect place, such the restroom or elevator of a business. Tempting labels on the bait, such as a payroll list or an appraisal list, will make it easy to input it into a computer.
-
Pretexting
Pretexting is an attack that makes use of a pretext to attract attention and persuade the target to provide information.
For instance, a poll on the internet could appear relatively benign at first, but subsequently ask for bank account information.
Or a person with a clipboard can appear and claim to be doing an internal system audit, but they might not be who they seem to be and might instead be trying to steal important information from you.
-
Tailgating
When unauthorized access is gained to a restricted location by physically getting around the security systems in place, this practice is known as tailgating.
-
Scareware
Scareware is a type of malware that uses a perceived threat to trick people into visiting harmful websites and purchasing malicious software.
Best Practices to Prevent Social Engineering Attacks
Think twice before sharing anything. And no, you shouldn’t be very concerned about these attacks. It is essential to prevent them. Here are some suggestions for helping.
-
Configure spam filters on high
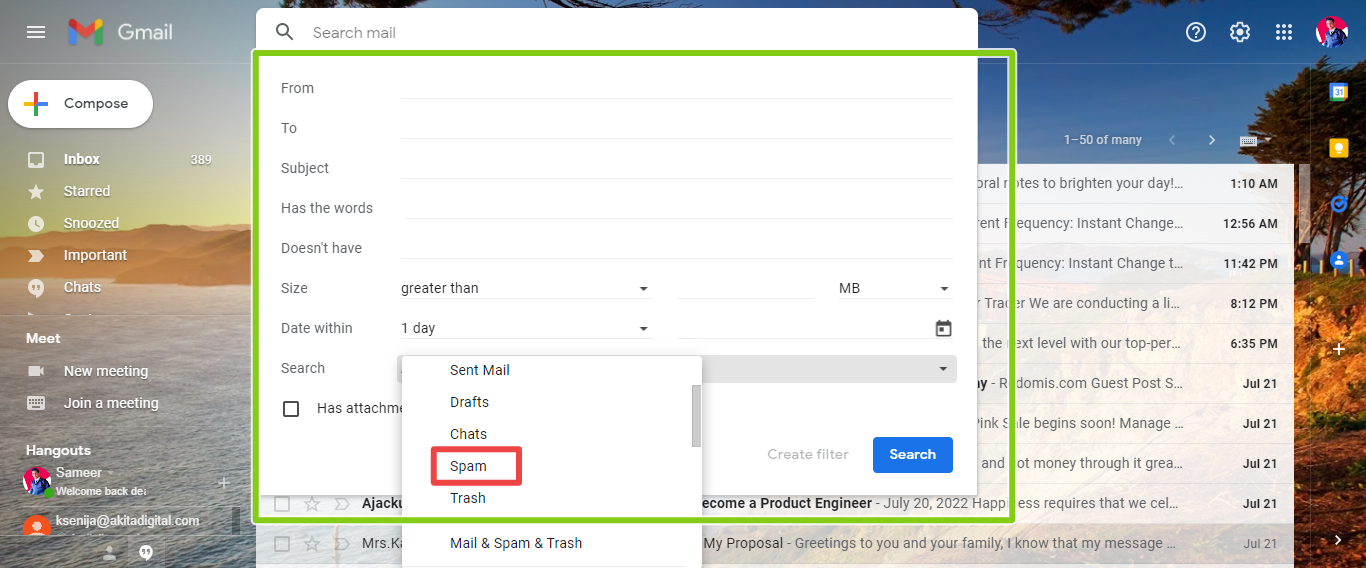
Spam filters are present in all email programs. Look carefully through your configuration choices and set the settings too high to find out. It will greatly assist you in avoiding spam texts.
By turning on spam filters, social engineering security risks will no longer be able to access your system.
Your inboxes are safeguarded against social engineering assaults by spam filters, which provide essential services.
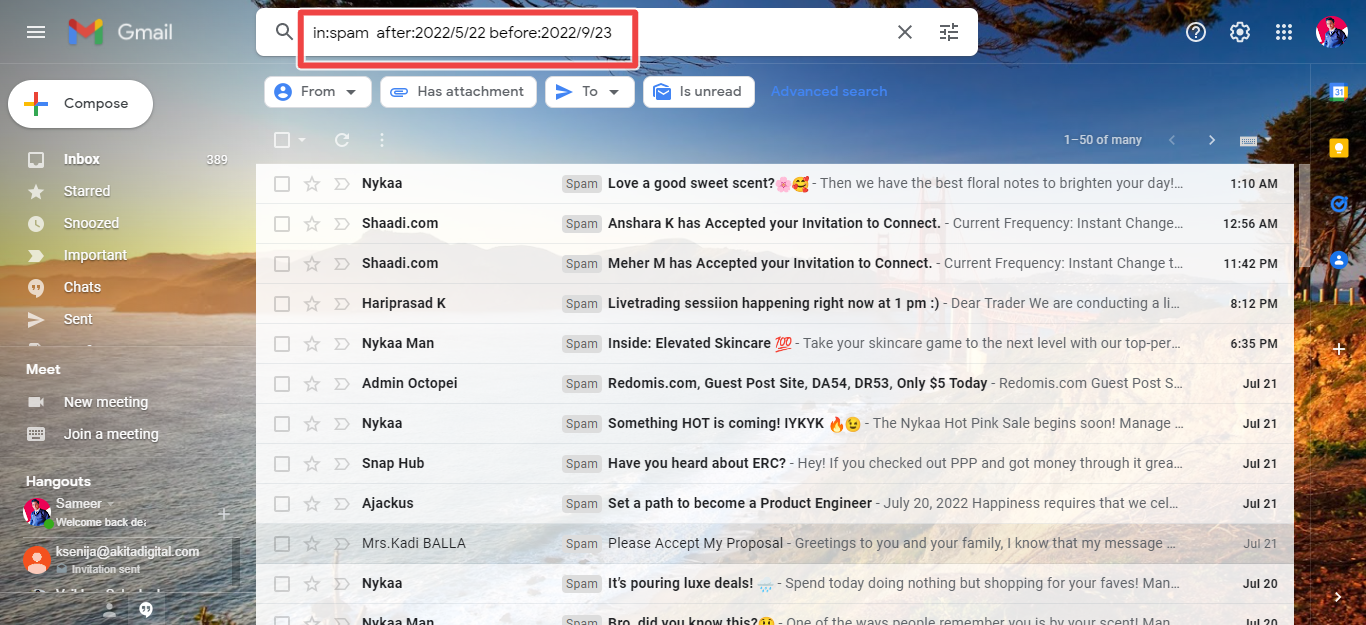
Spam filters are often provided by email service providers and retain emails that are deemed questionable. With spam features, you can easily categorize emails and avoid the dreadful responsibilities of recognizing suspicious emails.
Just keep in mind to check them often because periodically valid messages could be stuck there.
-
Never utilize the same password across several accounts

Once the attacker has control of one account, they can hack into more accounts.
Whether they are social or banking accounts, we frequently keep the same password for everything. We think that doing it this way will make it simple to remember a single password for all accounts.
However, attackers may use this as a chance to first compromise your social media passwords before moving on to your banking and other private accounts.
-
Encrypt your devices
Also, it’s critical to protect devices such that even a successful social engineering assault is constrained in what it can accomplish.
Regardless of whether it’s a smartphone, a simple home network, or a significant corporate system, the fundamental concepts remain the same.
• Keep your antivirus and anti-malware programs up to date.
• Consistently apply security fixes to software and firmware.
• Avoid using administrator mode on your PC, network, or rooted phone.
• A password should never be used across several accounts.
• Implement two-factor authentication for crucial accounts.
• If you just shared your password for an account and suspect you may have been “engineered,” immediately change the password.
• Remain current on emerging cybersecurity threats.
• Install, maintain, and update your email filters, firewalls, and antivirus software on a regular basis.
Note: These were only a few of the broad principles; the key aspects provide further detail.
-
Assure your security patches are up to date
To get unauthorized access to your data, cybercriminals typically hunt for holes in your application, software, or systems.
A security patch basically involves adding code to systems, programs, or software in order to “patch” the vulnerability. This strengthens the system’s defences against intrusion.
Always keep your security patches up to date and make sure that your web browsers and systems are running the most recent versions as a preventative step.
-
Employ multi-factor or two-factor authentication
Your account is no longer secured with just a password. To ensure that no outsider may readily access your accounts, use two or more methods of authentication.
Just as important are extra layers. It might be a captcha, a fingerprint scan, a security question, or SMS confirmation codes.
Social Engineering can be used to get access to the passwords. It is necessary to perform multi-factor authentication, which may involve using an OTP number, security questions, or Biometric Access.
-
When in doubt, immediately change passwords
Change all of your passwords right away if you believe you may have given your password to a spammer.
-
Educate the workforce
Keep your staff informed of the most recent social engineering dangers and assist them wherever required in exercising prudence.
-
Limit your speed
When you detect a sense of urgency entering a conversation, be very cautious. This is a typical tactic used by malevolent actors to prevent their victim from carefully considering the situation.
If you’re under pressure, go slowly throughout. Say anything to slow things down and allow yourself time to consider, such you need to obtain the information, you need to ask your boss, or you don’t have the correct information with you right now.
If social engineers realize they’ve lost the benefit of surprise, they’ll often stop trying to trick others.
-
Exit the loop
Sense of urgency is a common attribute in social engineering. Attackers believe their victims won’t give the situation much thought. Therefore, stopping to think for a second can stop these attacks or expose the perpetrators behind them.
Instead of handing up information over the phone or clicking a link, call the official number or navigate to the official website URL.
Check the source’s veracity via a separate communication channel.
For instance, if an acquaintance emails you asking for money to be wired, text them on their phone or give them a call to make sure it’s actually them.
-
Do not download unknown files
It’s best to ignore any emails with the subject line “URGENT” if you (a) don’t know the sender, (b) don’t expect anything from the sender, and (c) are unsure if you should read the file. By doing so, you completely eliminate your potential insider danger.
-
Refuse offers or pleas for assistance
Social engineers may approach you for information or may even volunteer to assist you (i.e., posing as tech support).
Any requests or offers from the sender should be regarded as a fraud if you did not ask for any assistance.
Before sending anything to the sender, do some independent investigation on them.
-
Consider your Digital Footprint
You might want to think about your digital footprint as well.
Social media oversharing of personal information might provide these crooks with additional information to work with.
For instance, if you maintain your CV online, you might want to think about hiding your home address, phone number, and date of birth.
For attackers who are preparing a social engineering threat, all that knowledge is helpful.
We advise you to keep your social media privacy settings set to “friends only” and to consider carefully before posting anything online.
-
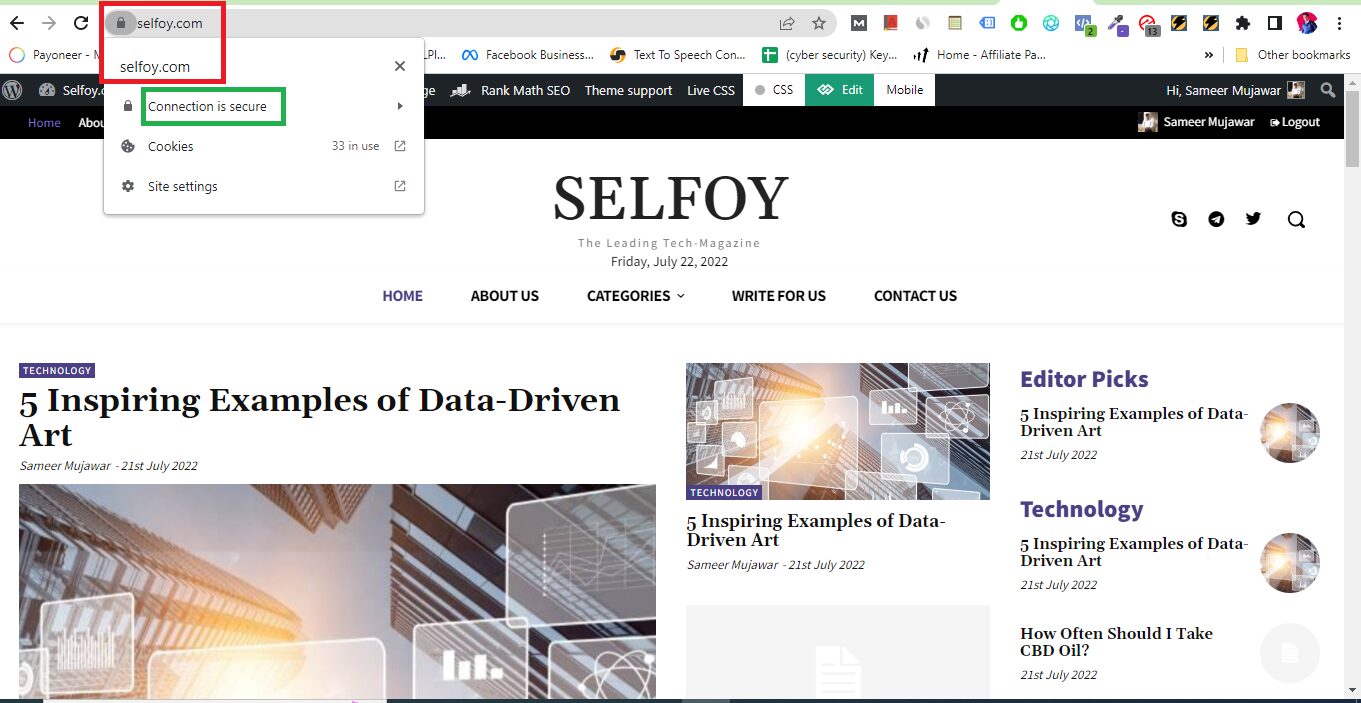
Check for SSL Certificate
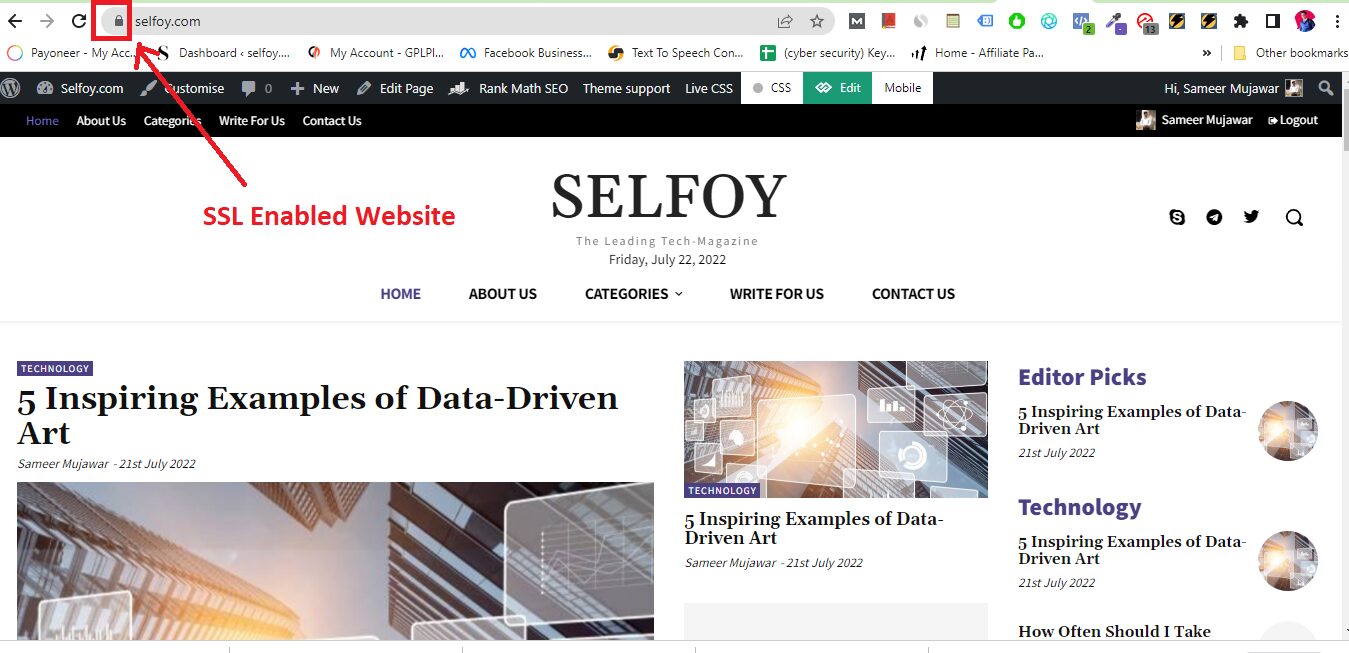
Even if hackers intercept your conversation, they won’t be able to access the information because data, Emails, and other forms of communication are encrypted.
By getting SSL certificates from reputable authority, this may be accomplished.
Additionally, you should carefully check the website before providing any important information. Examine the URLs to confirm the legitimacy of the website.
Websites that begin with https:// may be trusted as secure and encrypted. Websites beginning with http:// do not provide a secure connection.
-
Penetration Testing
An approved simulated assault is carried out on a computer system as part of a penetration test (pen test) to assess its security.
Penetration testers use the same instruments, tactics, and methods as attackers to find and demonstrate the financial impacts of a system’s vulnerabilities.
Your workers and the sorts of social engineering attacks you may be vulnerable to can be determined if your pen-tester is successful in putting your important system in risk.
-
Consistently keep a keen eye on critical systems
Ensure that your system, which contains critical information, is watched over 24 hours a day.
Trojans are only one example of exploitation techniques that occasionally rely on a system that is weak.
Web application scanning may be used to check both internal and external systems for vulnerabilities in your system.
Additionally, you should do a social engineering engagement at least once a year to see whether your staff may be vulnerable to social engineering risks.
If fraudulent domains are discovered, they can be immediately removed to prevent copyright violations online.
-
Always be wary of dangers
Any request for the right information you receive should be checked three times in total. Watch for cybersecurity news so you can respond quickly if you are the victim of a recent incident.
I advise signing up for a few morning newsletters to be informed on the newest developments in information security, such as Selfoy, Tech Advisor or E&T Magazine.
The most effective method for preventing social engineering attacks is to conduct a pen-test to look for and attempt to exploit weaknesses in your company. Other important precautions include setting spam filters on high, encrypting all devices, checking that your security patches are current, and configuring spam filters on high.
Conclusion
Thoughts came and went constantly as I was composing this article. How many times may I have disclosed my personal information? Filling up our personal information on various online signup forms, such as Mobile no , phone numbers and home addresses, has become so usual.
Therefore, wrote this article on the Best Ways to Protect from Social Engineering considering for both the benefit of our readers and for my own personal understanding.
And I came to understand that social engineering risks are becoming worse every day and are now among the biggest cyber hazards to companies of all sizes.
As a result, I urge all of our readers to provide your company with adequate defences against social engineering assaults.
Make sure your organization has the tools necessary to quickly identify security problems, keep an eye on what’s happening, and contact your security team so they can respond right away.
And even on a personal level, make an effort to maintain effective safeguards against social engineering attempts. Try to read many tech journals, like one of ours and, on a weekly basis so that you may stay current.
We really hope you enjoyed reading this post. Please keep reading to stay current on the newest trends and technology. Even if you might not be an expert in everything, starting out with it might still be a good idea.







