Network firewall and host based firewall
A computer network involves communication interaction between a single user with a single server or multiple users with multiple servers’. The communication is of data and information that is allowed and denied within the operating system or on a global network.
Every one of us uses the operating system, be it on a mobile or computer, the computer network is a set of work taking place every second not visible to us. The network is massive and complex and it is expanding every second, as it is reliable to everyone which makes our job easy and saves our time.
Firewall security.
The number of resources or data being exchanged every day does not have a boundary and its anonymity can make any system vulnerable. A firewall is something of a wall between two or multiple ends protecting any unwanted guest to interfere with the network and/or the system.
A firewall can be a hardware, software, or both preventing not just the outside interference but also preventing exposure and access of vulnerable data to be shared outside, protecting local or sub-network from the global network.
There are two types of Firewall security
A firewall filters traffic to defend with a certain access control list using its security policy.
The rules are meant to identify the infiltration using the network and transport of the communication system of the computer network.
A firewall uses pocket filters, Stateful inspection, application proxy gateways, circuit-level gateways (VPN), Guard firewall, encryption, and decryption to control the outside network and manage the environment inside as well. A vulnerability is determined by the organization that operates the firewall.
Any form of infiltration can be inspected in the network or the system itself.
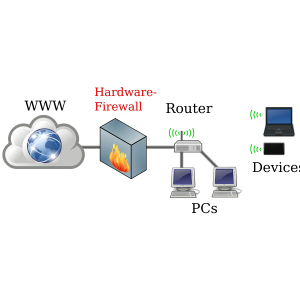
Network Firewall
A network firewall is a hardware and/or software-based protection. being the first line of defense protects everything on the network. It filters traffic from the internet to LAN and vice versa, allowing and denying access to the internet.
A physical form of network firewall connects to a LAN or switch of ethernet connects with multiple devices or systems. This system of defense is mostly used by big organizations as it protects multiple OS.
A network can have a stand-alone firewall for large organizations whereas a router can be used by small organizations. A large enterprise may also consider using cloud-provided services. Using virtual storage or a system in the cloud, your security will be ensured by a firewall in their system or the network. A cloud service can be public or private.
Host firewall
A host-based firewall is a software application system protecting and decrypting the attacks that happen by installing its software in the system. It is the second layer of protection and can easily defend working as part of an operating system.
Read Also: Best network home security (NVR) camera system: Priced lower to higher.
No matter how secure you will be, your common information like email is circulating on the internet and there is possibly a phishing email sitting in your main index or an error file and application in your system. Remember a hacker can shut down your firewall software. One must make sure and buy a good service provider in terms of security.
A simple example:
Imagine you are in a house surrounded by a boundary with one single gate. There is a watchman at the gate and a bodyguard in your house. The house is your operating system, the boundary differs between your system and the online global world, the watchman is the network firewall that is supposed to let familiar people inside and uninvited people outside and the bodyguard is a host firewall who will beat the hell out if someone breaches inside the house.
Now, a malicious intruder can also take down the bodyguard, therefore a watchman is required, depending on where you consider security.
| Network firewall | Host firewall |
| Hardware device. | Software device. |
| Mostly used by giant enterprises. | Personal computers as well as big enterprises. |
| Inflexible in nature in terms of its physical arrangement. | Flexible in nature in terms of mobility. |
| With-in the network | In a particular system. |
| Difficult to infiltrate. | Can be infiltrated if not used correctly. |
| Strong encryptions. | Difference is limited compared to network firewalls. |
| Low maintenance once installed. | Maintenance and surveillance by the service provider of the hosts firewall. |
| Easy to manage cia software by firewall administrator or manager. | Difficult to manage as the number of hosts increases. |







